5) Sign your code
This last step is the one you will perform most often. It requires two files:
- the file to be signed (.exe .msi .cab …) before publication
- the secret file code_signing.pfx
👀 Visual
⚙ 1/1 Sign
Use this command to sign the file HelloWord.exe
signtool sign /debug /fd sha256 /f code_signing.pfx /tr http://timestamp.digicert.com /td sha256 HelloWord.exe
Note: The original HelloWord.exe file is overwritten with its signed version.
/tr http://timestamp.digicert.com is important. It returns a certified timestamp that will be included with the signature.
This allows the signature to be accepted even after the certificate included in code_signing.pfx has expired.
These url can also be used:
• http://time.certum.pl
• http://timestamp.sectigo.com
• http://timestamp.globalsign.com/scripts/timstamp.dll
👉 To avoid being banned, space out your requests by approximately 15 seconds ;-)
🕮 Manual for signtool sign
🔍 Verify (level 1)
-
Right click on the signed file (
HelloWord.exe) > click on ‘Properties’ > click on the ‘Digital Signatures’ tab
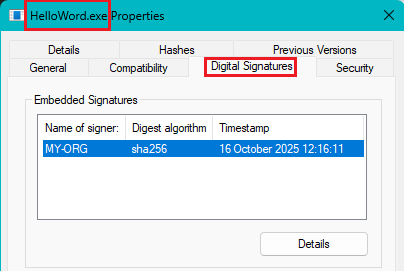
- Select the ‘signer’ (it is you as a developer) > Click on ‘Details’
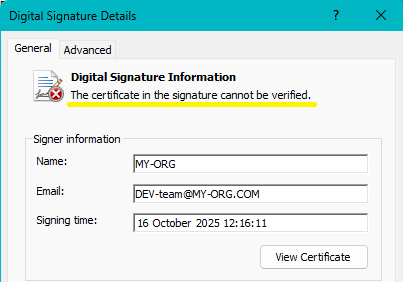
Notes:
- The certificate in the Countersignatures section (not in the picture) is the one for the timestamp.
- ‘The Certificate in the signature cannot be verified’ because your private CA certificate is not (yet) know by Windows.
If you click on the ‘Advanced’ tab you can see who is the ‘Issuer’: you as a CA.
- The certificate in the Countersignatures section (not in the picture) is the one for the timestamp.
- Click on View ‘Certificate’
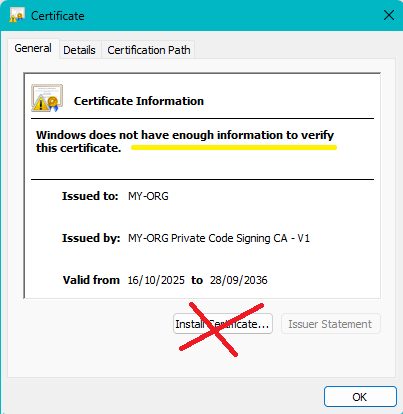
On this popup you see your private RootCA and the Code Signing Certificate
If you click on the ‘Details’ tab you will see all fields of the certificate.
DO NOT click on ‘Install Certificate’.
🔍 Verify (level 2)
Now, as a user of your software, install the private CA certificate myRootCA.crt published by MY-ORG
(as explained here) and check again the Digital Signatures of HelloWord.exe. You should get this:
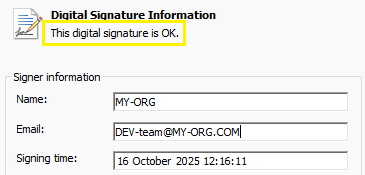
Click on ‘View Certificate’
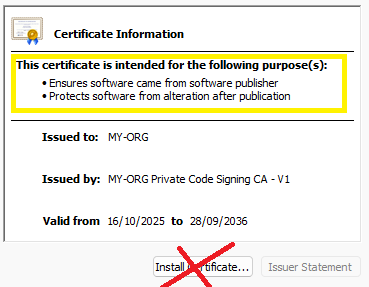
DO NOT click on ‘Install Certificate’.
Click on the ‘Certification Path’ tab
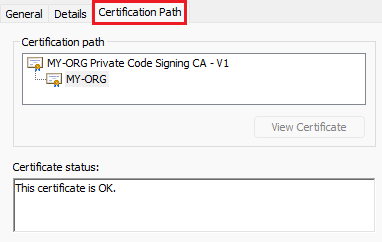
if this verification was successful, this means:
- your private CA certificate (
myRootCA.crt) is valid 🡆 It can be published - your certificate for signing code (
code_signing.pfx) is valid 🡆 It must stay secret - HelloWord.exe has a valid signature. 🡆 It can be published.
📌 Last but not least
Users of your signed files will have to import the myRootCA.crt file into their Windows key store.
You must therefore publish myRootCA.crt and its thumbprint .
See last paragraph of step 1 for more details.